Topic 23
The need to authenticate information by Vaibhav Bhandari
What is authentication? And why is it so important?
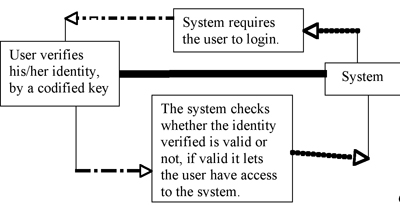
In a world full of innovative ideas, authenticating information online is becoming necessary, as its presence prevents us from facing consequences that lead towards several ethical and social issues. Authentication is the act of establishing or confirming something. This is becoming a neccesity and is vitally important, as it provides a safe and trustable network. In more simpler words authentication is the process which enables to verify a digital identity of a sender. It is a key aspect of trust-based identity which provides a codified assurance of one user to an another user. A common example of this is a request to log in. This can be things such as credit card numbers, and passwords.
Places where information needs to be authenticated
• Accesing Email’s
• Using an Internet Banking System
• Withdrawing cash from an ATM machine
*In all these places a login is needed, therefore inorder to login to the system it requires for the user to verify his identity by codified passwords.
What are the consequences if there is no authentication?
In simple words if there is no authentication it would enable anyone to access any indentity and manipulate or destroy data. More precisely it would become possible for anyone to login into any place, where in the presence of authentication it would require a user to verify his/her identity. This would mean that systems without the presence of authentication wouldn’t require a login and anyone could log onto anywhere that they wish to login. Hence this brings up various consequnces which result into several social and ethical issues.
Visual Demonstration
A demerit of Authentication – Phishing
One of the most major consequences faced because of authenticating information is as a result of phishing. Phishing is a criminal activity using fraud computer techniques (social engineering). The main objective of phishing is to fraudely acquire sensative information. Meaning to falsely acquire credit card numbers and passwords. This is usually done by sending a disguised email or a disguised announcement and asking the users to verify their identity. In this case they are not actually veryfying their identity but they are actually providing their sensative information to the phishers.
Major questions to be considere when writing the IB exam-
1. What is an alternative to authentication? Is it reliable? Is it secure?
2. What is a solution to the demerits of authentication? (What is a solution to phishing?)
3. What are the impacts of Authentication globally and locally? (What are the issues arised by phishing?)
10 Comments:
- said...
-
yea quite a bit of information but u didnt talk about the issue that people forget their login and pass. which is a big problem...
- said...
-
In the case of when people forget in their password or username, the system basically just asks the user to verify himself with alternatives. Such as in most email cases secter question or the system gives you another oppurtunity to change your password by it sending you a message on a previosuly provided account/email. However this has always been a problem as people can take advantage of this and access a system with a identity which is false and doesnt belong to them. Here is a video which shows how this can be done and this is known as the ERD method by which any password can be resetted on a pc http://www.metacafe.com/watch/
312243/hacking_win_xp_password/
- said...
-
Overall, well explained, and good usage with the diagram. I have to say that i agree authentication in this age is very important, seeing that people are shopping, using corporate emails, etc. on the internet. It is sad that people abuse authentication like you said, by using sofisticated phishing methods. Just recently, an anomynous user successfully made West Point Academy cadets send emails with personal information included.
- said...
-
Nice, but you didn't write about people misusing authentication to gain other people's passwords, which is a big issue in someplaces.
- said...
-
By the way, the use of the diagram and your other various techniques made the essay much easier to understand.
- said...
-
How powerful are such login-logout systems? it is possible to hack almost anything today! How do we propose to avoid haking, I mean, the possiblity is always out there. A system is never effcient if it is easily cheated.
- said...
-
yes again tomer i completely agree with you. As i said in today's world if you invent something there are always pro's and con's for that. You cannot fully avoid to con's but you can minimize them to the best by working safely.
- said...
-
As mentioned above, this topic needs further discussion. Perhaps a good mention here is new methods of authentication such as biometrics. It's harder to steal someone's fingerprint and retina than a bunch of letters and numbers.
- HeeJun Son said...
-
Well, although your essay is not bad, it could have been better if you had included and explained things in more details. For instance, you could have answered and explained the last IB questions instead of just leaving them. I could understand your thoughts easily though.


Very well explained, but I think the topic should be discussed further.